-
Tags
-
Author
-
Luísa Lima, Co-Founder & VP Engineering
-
October 8, 2019
Why startups should upgrade security with Zero Trust
Being one of the first team members at a startup is an adventure. Technical founders usually think that they will build the company of their dreams, based on the most recent programming languages and technologies. Initially, they imagine flawless processes: from following state-of-the-art development practices to practicing BDD and TDD, all with a 100% code coverage.
They are confident that everything will work smoothly. They visualize development work with complete specs, acceptance criteria, and continuous integration. They expect that deployments will be an absolute breeze, documentation complete, and powered by the latest infrastructure-as-code hype. DevOps will be self-managed and straightforward. Right?
Expectations vs. reality
When the day-to-day reality of startup life kicks in, founders are swamped by long lists of features to develop in record time. Suddenly, they are struggling to keep up with sprint schedules and that perfect-world development process can be lost in the rush to release. What usually does not come to mind when starting, especially in a small startup, is security.
Startup founders often do not have the time or headspace to consider security practices. Their time is consumed by more immediate challenges like figuring out why, just before a critical demo to an investor, the code written last week has mysteriously stopped working. We’ve all been there. Still, with today’s global work teams, startups must modernize their security operations to match their development processes and protect their intellectual property from the start.
Secure access without the slowdown
Startup founders do not want to think about closing access as they ramp up operations to get the first MVP out the door. They need solutions to provide practical and affordable access. At Fyde, our team is split between Europe and the US. Our developers, like most startups, don’t follow typical business hours and need to access data whenever inspiration strikes. Founders want every new developer, whether on payroll or a freelancer, to be able to start working productively from the get-go.
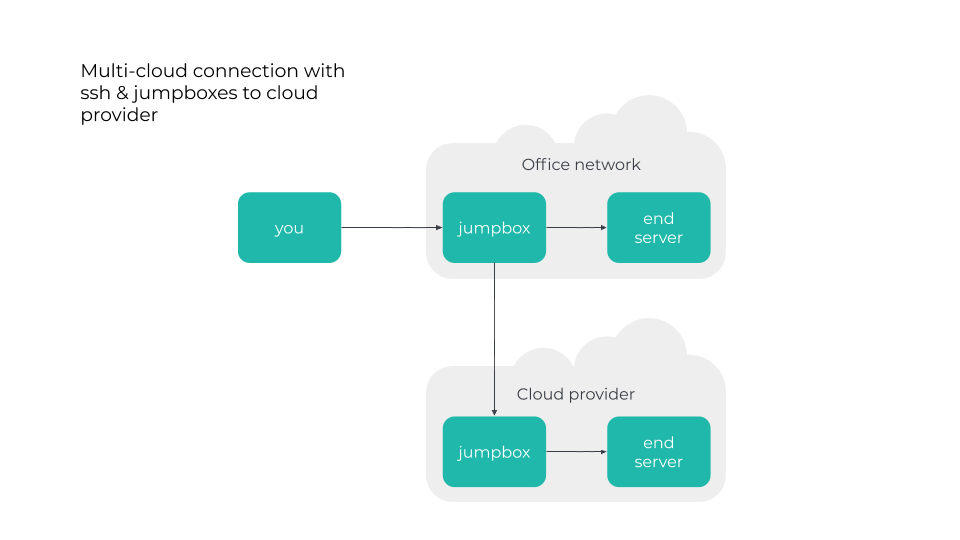
When there are just one or two developers, it’s easy to deploy the "home" setup: "SSH all things." You either open up SSH directly to your cloud instances or decide to be more cautious and set up SSH port forwarding and a jumpbox:
Growth challenges
As the business grows, the requirement list grows exponentially and the team expands. You might have a friend who offers to help with QA. Your marketing and sales allrounder showcases a feature that is still in an undeployed branch, in a build that is hidden somewhere in an artifact in S3. Suddenly, jumpboxes and SSH are not practical anymore.
In the midst of this chaos, you decide to set up a VPN to allow for these impromptu access requests. Here is the usual architecture:
.png?width=960&name=Technical%20diagrams%20v0.0%20(1).png)
Setting up an OpenVPN isn't hard. Many online tutorials provide straightforward instructions. However, when you set up a VPN, you open the door to your entire office network to the Internet. And you can bet that someone on the business team will share their private key to provide access for a friend. Faced with these issues, how can a fledgling startup balance the need for business agility with security realities? Zero trust is a good first step.
How Zero Trust can help
It’s a common misconception that strong security slows productivity. On the contrary, modern security practices can improve network accessibility and speed, protect data and save time.
Zero Trust replaces complex, network-draining VPNs with a new model that assumes the network is hostile. While this sounds contradictory, this assumption frees you to reimagine security. Network locality is not sufficient for establishing trust, and every flow must be authenticated and dynamically authorized. This creates an effective separation between the control plane – the supporting system that implements the flow authentication and authorization according to the defined policies – and the data plane.
Startups do not need in-house security expertise or complicated constructs to get started; cost savings add an extra incentive.
To learn more about Zero Trust, check Zero Trust Networks: Building Secure Systems in Untrusted Networks and the BeyondCorp paper by Google.
Learn more about Zero Trust:
What is Zero Trust and how can it transform your enterprise security?
Fyde: Zero Trust architecture and components
Remote workers need a security upgrade. How Zero Trust can help
Try Fyde
The theory sounds good, but where to start in practice? Try Fyde and easily set up Zero trust in your company. Check out our tech docs or contact us to set up a free POC.